The “Black Box” Architecture
agent-c is not a SaaS API; it is a Cryptographic Cleanroom.
The Risk Engine
Our engine implements a proprietary, weighted risk methodology protected by international patent. This logic is hardcoded into the enclave to ensure “Freedom to Operate” for our partners.
Core Methodology
The patented approach defines a methodology for:
- Binding multiple data sources (KYC, AML, Ownership) into a single attestation
- Calculating risk using a weighted formula with configurable parameters
- Producing cryptographically signed certificates suitable for regulatory compliance
The Formula
Unlike standard providers who conflate Identity with Ownership, our engine utilizes a proprietary, weighted methodology that decouples these elements. This granular approach prevents false positives and ensures verified control.
The Three Components
| Component | Source | Measures |
|---|---|---|
| KYC | Identity Verification Partner | Identity verification, PEP screening, jurisdiction risk |
| AML | Blockchain Forensics Partner | Wallet forensics, transaction history, sanctions exposure |
| KYW | CryptoPass | Cryptographic ownership proof (the “missing link”) |
Verdict Logic
The engine produces three possible verdicts:
- APPROVE - Low risk, verified ownership → Green Lane
- REVIEW - Borderline scores → Manual review queue
- REJECT - High risk or unverified ownership → Blocked
The Enclave (Intel SGX)
The scoring logic runs inside a Trusted Execution Environment (TEE).
Security Guarantees
- Sealed Memory: Even the node operator cannot see the input data
- Remote Attestation: The code proves to the network it hasn’t been tampered with
- No Persistence: PII is processed in-flight and never stored
Future: TON Cocoon
We are planning migration to the TON blockchain’s confidential compute infrastructure (“Cocoon”) for decentralized attestation.
The “Green Lane” Logic
We act as a pre-filter for banks:
Lane Classification
| Lane | Criteria | Bank Action |
|---|---|---|
| Green | Low risk + verified ownership | Auto-accept certificate as EDD |
| Yellow | Borderline scores | Request underlying data for manual review |
| Red | High risk or unverified | Reject transaction |
Why This Works
Banks don’t want to store passport scans and wallet histories. By accepting a signed certificate from a trusted enclave, they get:
- Compliance coverage - The certificate documents their due diligence
- Reduced liability - They never touch the raw PII
- Audit trail - Every certificate has a unique ID and signature
Dusting Attack Mitigation
A sophisticated feature of our AML engine is dusting mitigation.
Hackers perform “dust attacks” by sending tiny amounts (< $10) from mixer wallets to taint innocent addresses. Our engine:
- Detects when bad triggers (mixer/darknet exposure) exist
- Checks the total exposure amount
- Ignores triggers below the $10 dust threshold
This prevents false positives that would unfairly penalize legitimate users.
Configurable Methodology
Component weights are configurable for specific jurisdictions or use cases. Weight changes require redeployment to the enclave to maintain attestation integrity.
Technical details available to licensed partners.
Reference Implementation: The Developer Console
We provide a functional Telegram Mini App to demonstrate the compliance flow in real-time.
| 1. Connect & KYC | 2. Verify Ownership | 3. Generate Certificate |
|---|---|---|
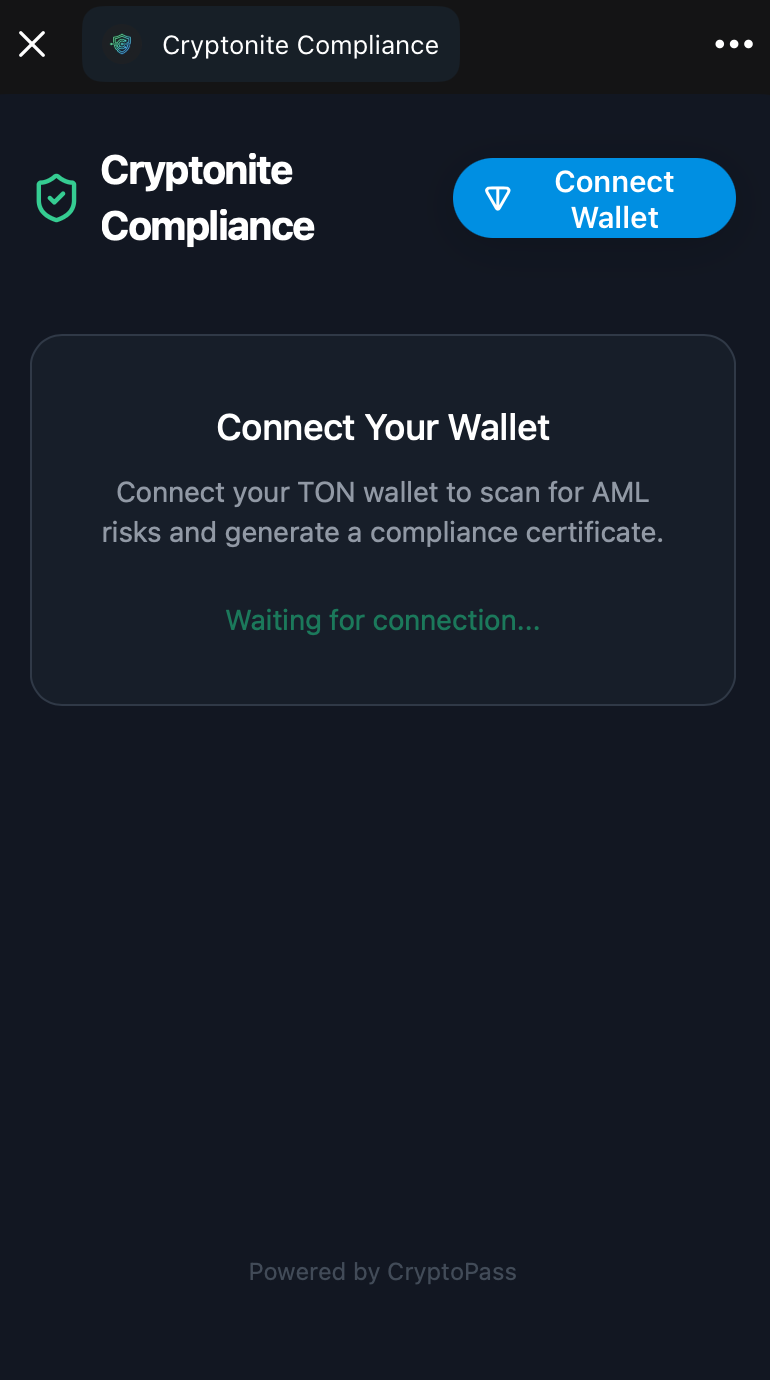 |
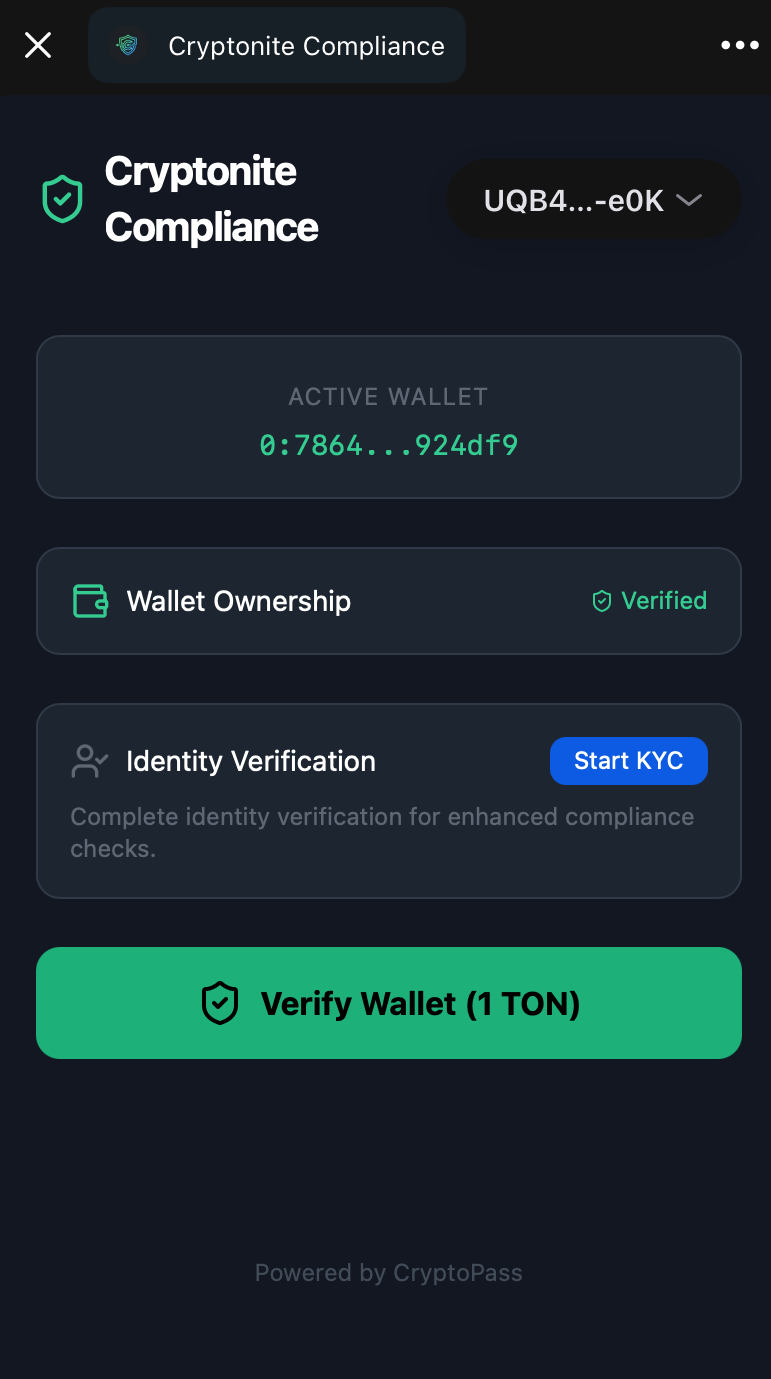 |
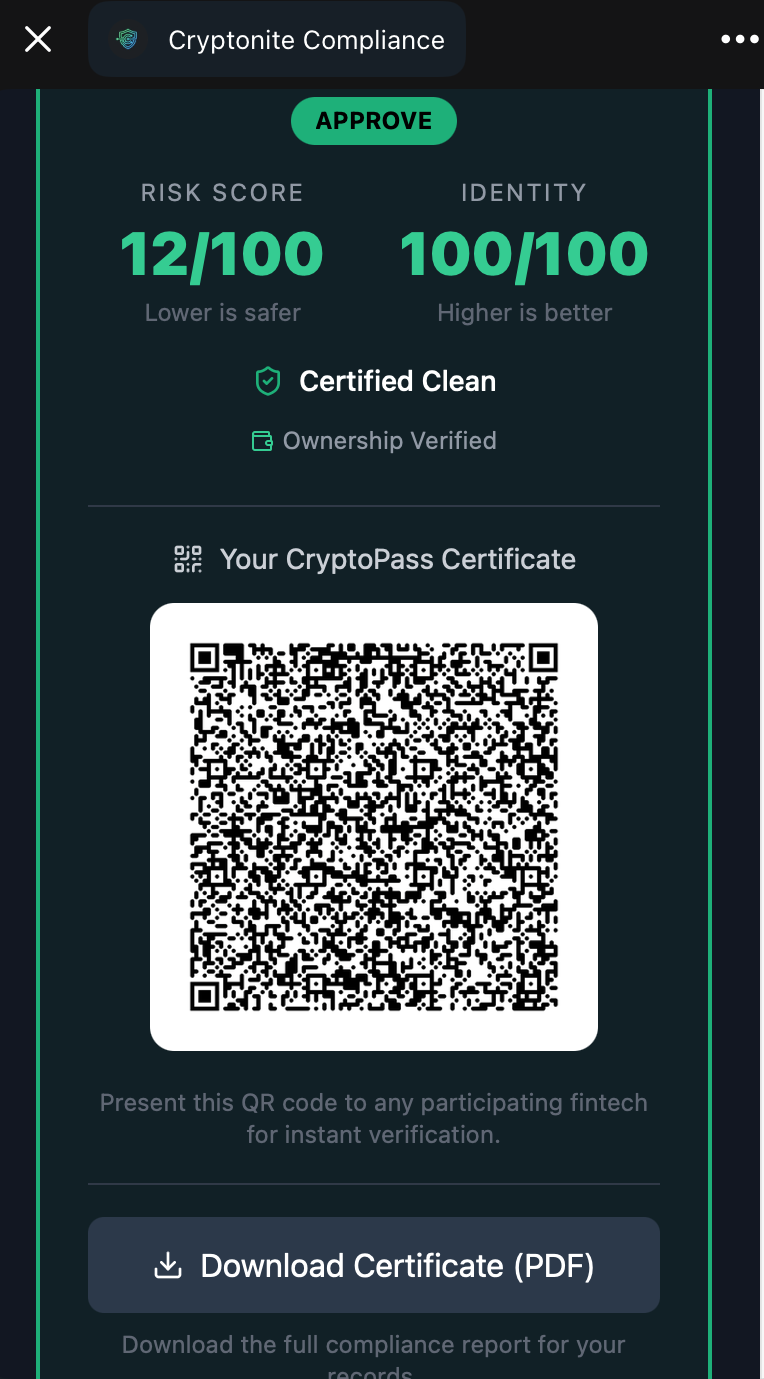 |
| User links wallet and identity. | Cryptographic signature proves ownership. | agent-c issues the signed asset. |
| ← Back to Home | Partner Access → |
